Security Roles
Security Roles are a way of restricting Analysts' access to different parts of vFire Core. Instead of defining access permissions for each Analyst in the system, you simply create a security role, assign permissions to that role, and then assign the role to whoever needs these permissions.
Controlling access to different parts of the system is important. Often, large numbers of analysts need the same access permissions. For example, fifty members of staff working on the service desk all need the same permissions. It would be inefficient to set up specific permissions for each of them, so instead, you can create security roles for different areas of the system, each with their own set of permissions, and then simply assign security roles to each Analyst. Then every Analyst with the same security role will have the same access permissions.
You can define security roles for:
| General Access | which covers basic vFire Core Administration rights and Timesheet permissions, including maintaining security roles |
| IPK Management | which covers permissions for calls and related entities. It also includes permissions for Call screen sets, IPK groups (including default groups), IPK statuses, IPK streams, and forms |
| Workflow Management | which covers permissions for the workflow (change, release, configuration management) request procedures in vFire Core |
| Configuration Management | which covers permissions for managing configuration items, services and related entities within the CMDB. It also includes permissions for viewing, creating, updating and deleting CMDB item details, attaching objects to CMDB items and forms |
| Service Level Management | which covers permissions for agreements in vFire Core including Service Level Agreements (SLAs), Operating Level Agreements (OLAs) and Underpinning Contracts (UCs) |
| Reporting | which covers permissions for viewing, creating, designing, and scheduling reports within vFire Core |
| Availability Management | which covers permissions for viewing, creating and updating Outages, Schedules and viewing Availability Data for CMDB items |
| Knowledge Management | which covers permissions for viewing, creating and editing knowledge entries within the Knowledge Bank |
| Bulletin Board | which covers permissions for viewing, creating and editing Bulletins |
For convenience, each type of security role comes with a pre-defined role called “All”. Typically, this role has all the options enabled, but not always. You can redefine what options are available to suit the needs of your organization. You can also use this role to create other roles that suit your organization’s requirements.
Creating a Security Role
Before you start
You must have Security Roles setup selected in your own General Access security role before you can assign or remove permissions for any security roles.
-
Select the Menu button
 , then Admin, and then select System Administration. The System Administration window is displayed
, then Admin, and then select System Administration. The System Administration window is displayed  . In the Explorer pane, locate the System group
. In the Explorer pane, locate the System group  , scrolling up or down if necessary. You may need to expand the group to see the options within it.
, scrolling up or down if necessary. You may need to expand the group to see the options within it.Expand the Security Roles group in the Explorer pane
 , scrolling up if necessary. Select the type of role you want to view from the list in the Explorer pane. A browse table displays all of the existing roles of this type. Now you can create, update or rename a security role of this type.
, scrolling up if necessary. Select the type of role you want to view from the list in the Explorer pane. A browse table displays all of the existing roles of this type. Now you can create, update or rename a security role of this type. The pre-defined role All typically has all role options selected. However, some of the options are not selected by default and you should explore the permissions set before assigning the role.
-
Select
 .
. - Key the name of the role you want to create into the Role Name field.
- Select the permissions you want associated with the role. The fields available will vary depending on the type of security role.
Viewing a Security Role
Before you start
You must have Security Roles setup selected in your own General Access security role before you can assign or remove permissions for any security roles.
-
Select the Menu button
 , then Admin, and then select System Administration. The System Administration window is displayed
, then Admin, and then select System Administration. The System Administration window is displayed  . In the Explorer pane, locate the System group
. In the Explorer pane, locate the System group  , scrolling up or down if necessary. You may need to expand the group to see the options within it.
, scrolling up or down if necessary. You may need to expand the group to see the options within it.Expand the Security Roles group in the Explorer pane
 , scrolling up if necessary. Select the type of role you want to view from the list in the Explorer pane. A browse table displays all of the existing roles of this type. Now you can create, update or rename a security role of this type.
, scrolling up if necessary. Select the type of role you want to view from the list in the Explorer pane. A browse table displays all of the existing roles of this type. Now you can create, update or rename a security role of this type. The pre-defined role All typically has all role options selected. However, some of the options are not selected by default and you should explore the permissions set before assigning the role.
-
To view or update a security role, select the role in the browse table and select
 .
. - The details window is displayed. It may have several tabs, each containing different settings. Select the relevant tab to view the information you wish to examine.
Updating a Security Role
Before you start
You must have Security Roles setup selected in your own General Access security role before you can assign or remove permissions for any security roles.
You can update any of the details already set for a security role, including the name. Analysts who already have the security role assigned are affected by any changes.
- View the security role.
- Make the updates. The fields available will vary depending on the type of security role.
Renaming a Security Role
Before you start
You must have Security Roles setup selected in your own General Access security role before you can assign or remove permissions for any security roles.
You can rename roles which are currently in use or assigned to active Analysts. The name will be updated in the person details for the Analysts affected..
-
Select the Menu button
 , then Admin, and then select System Administration. The System Administration window is displayed
, then Admin, and then select System Administration. The System Administration window is displayed  . In the Explorer pane, locate the System group
. In the Explorer pane, locate the System group  , scrolling up or down if necessary. You may need to expand the group to see the options within it.
, scrolling up or down if necessary. You may need to expand the group to see the options within it.Expand the Security Roles group in the Explorer pane
 , scrolling up if necessary. Select the type of role you want to view from the list in the Explorer pane. A browse table displays all of the existing roles of this type. Now you can create, update or rename a security role of this type.
, scrolling up if necessary. Select the type of role you want to view from the list in the Explorer pane. A browse table displays all of the existing roles of this type. Now you can create, update or rename a security role of this type. The pre-defined role All typically has all role options selected. However, some of the options are not selected by default and you should explore the permissions set before assigning the role.
- Select the role you want to rename. The entry is highlighted.
- Overtype with the name you want to use for the selected role.
- Select
 to save the changes and close the window. Provide the Change Reasons if prompted to do so. Alternatively, select another tab, if appropriate.The security role name is automatically updated in the details of all Analysts with that name assigned.
to save the changes and close the window. Provide the Change Reasons if prompted to do so. Alternatively, select another tab, if appropriate.The security role name is automatically updated in the details of all Analysts with that name assigned.
Deleting a Security Role
Before you start
You must have Security Roles setup selected in your own General Access security role before you can assign or remove permissions for any security roles.
You can delete roles which are currently in use or assigned to active Analysts. The Analyst’s role for the function will default to None.
-
Select the Menu button
 , then Admin, and then select System Administration. The System Administration window is displayed
, then Admin, and then select System Administration. The System Administration window is displayed  . In the Explorer pane, locate the System group
. In the Explorer pane, locate the System group  , scrolling up or down if necessary. You may need to expand the group to see the options within it.
, scrolling up or down if necessary. You may need to expand the group to see the options within it.Expand the Security Roles group in the Explorer pane
 , scrolling up if necessary. Select the type of role you want to view from the list in the Explorer pane. A browse table displays all of the existing roles of this type. Now you can create, update or rename a security role of this type.
, scrolling up if necessary. Select the type of role you want to view from the list in the Explorer pane. A browse table displays all of the existing roles of this type. Now you can create, update or rename a security role of this type. The pre-defined role All typically has all role options selected. However, some of the options are not selected by default and you should explore the permissions set before assigning the role.
- Select the role you want to delete. The entry is highlighted.
- Select
 . If the role is in use, you will receive the following warning: :
. If the role is in use, you will receive the following warning: :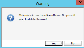
- Select
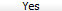 to confirm the deletion. The entry is deleted from the window but it is not yet deleted from the database.
to confirm the deletion. The entry is deleted from the window but it is not yet deleted from the database. - Select
 to delete the role from the database and close the window. Provide the Change Reasons if prompted to do so.
to delete the role from the database and close the window. Provide the Change Reasons if prompted to do so.
Restoring a Deleted Security Role
Before you start
You must have Security Roles setup selected in your own General Access security role before you can assign or remove permissions for any security roles.
-
Select the Menu button
 , then Admin, and then select System Administration. The System Administration window is displayed
, then Admin, and then select System Administration. The System Administration window is displayed  . In the Explorer pane, locate the System group
. In the Explorer pane, locate the System group  , scrolling up or down if necessary. You may need to expand the group to see the options within it.
, scrolling up or down if necessary. You may need to expand the group to see the options within it.Expand the Security Roles group in the Explorer pane
 , scrolling up if necessary. Select the type of role you want to view from the list in the Explorer pane. A browse table displays all of the existing roles of this type. Now you can create, update or rename a security role of this type.
, scrolling up if necessary. Select the type of role you want to view from the list in the Explorer pane. A browse table displays all of the existing roles of this type. Now you can create, update or rename a security role of this type. The pre-defined role All typically has all role options selected. However, some of the options are not selected by default and you should explore the permissions set before assigning the role.
- Select Show Deleted to include deleted roles in the list of defined roles.
- Select the role entry you want to restore. The entry is highlighted.
- Select
 to restore the deleted role.
to restore the deleted role. - Select
 to delete the role from the database and close the window. Provide the Change Reasons if prompted to do so.
to delete the role from the database and close the window. Provide the Change Reasons if prompted to do so.